Authentication and Authorization in a Microservices Architecture
Authentication and Authorization are critical issues in any IT system that deals with swnsitive informations. A distributed system as an Event-Driven collection of Microservices running on the cloud adds additional challenges for these issues.
This post recapitulates the characteristics of an Event-Driven Microservices Architecture, what is Authentication and Authorization, explains the requirements for a Solution, and finally proposes a solution that addresses these requirements.
Microservices Architecture
All companies to survive and grow need to embrace, adapt and innovate with technologies that can improve and change their business models and operations to enable a more competitive business relationship with the market. Digital technologies are evolving fast and having widespread adoption. The current business scenario is been reshaped by transformations enabled by these technologies, enabling new business models and turning others obsolete. Most of the successful startups use the Lean Startup Method, for fast discovery and implementation of new business models.
The Build, Measure, Learn Cycle is the most important model of the Lean Startup Method. It is described in the book The Lean Startup by Eric Ries from 2011. What exactly does the Build, Measure, Lean Cycle entail?
- Build - make a prototype quickly or develop another method that allows you to test your hypothesis quickly and accurately.
- Measure - measures the results.
- Learn - learn from the results. This gives you new ideas to improve your product or service.
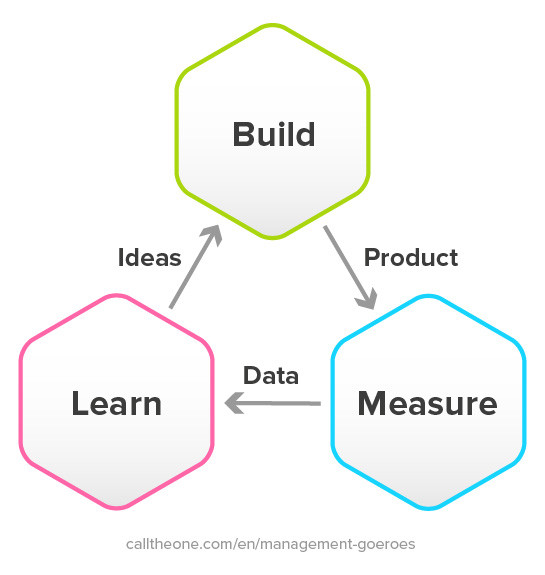
After this, repeat these three steps (this is the Cycle). An important part of the Lean Startup Method is that the company that can repeat the above process the fastest will eventually win.
IT systems are the main tool to implement business models and operations and are an enabler of the Lean Cycle. Microservices Architecture is the prominent software architecture that addresses the needs of current IT systems. It has the following characteristics:
- Composed by autonomous specialized services.
- Each service is intrinsically related to a business subdomain.
- Multiple technologies: each service can be implemented using the most convenient technology.
Event-Driven Microservices
If the business model and operations are implemented by its IT systems, the IT systems should be:
- Secure,
- Available,
- Reliable
- Scalable
Event-Driven Microservices is a software architecture aimed to support availability, reliability, and scalability. It helps to deliver consistent customer experience while addressing failures and performance issues. It is based on:
- Loosed coupled services
- Intercomunication via messages
Authentication
Identification of the user. To check the identity of an user based on the credentials received. The identification of an user can be composed of atributes that define roles. The authentication can be a system service.
Authorization
Permissions assigned for an user. To determine if the identified user should be granted access to a particular resource. Authorization can be specific for each service. User relationships with domain data are determined in the service context. Resource server.
Requirements for a Solution
- Authentication in the first interaction in a user session
- Authentication Persistance during a user session
- Existence of a Mechanism for Authentication invalidation during a session
- Authorization based on user, context and data
- Minimal overhead in each Microservices
A solution
Client / Server Communication:
- Cookies as transport mechanism
- JWT for storing pertinent information about the user
System Components:
- Authentication Service
- Authorization Service
- Message Mechanism
Microservice add-ons:
- Authentication Sidecar
- Autorization Sidecar
Data based Authentication and Authorization
JWT are access tokens JWT enables stateless authorization
Json Web Token is a compact URL-safemeans ofrepresenting claims to be transfered between two parties. The claims are encoded as JSON object that is digitaly assigned by hashing itusing a shared secret between the parties.
A secure way to transit to encapsulate arbitary data that can be sent over unsecure URLs. Securely send a payload. A JWT is composed of a Header, a payload (claims), and a signature.